Quickly add your Customer End Users via Active Directory or Okta with Startly’s End User Sync integration. Administrative access to network users and/or a Super User with LDAP (Lightweight Directory Access Protocol) access is required to properly configure a sync.
Add a New Sync Configuration
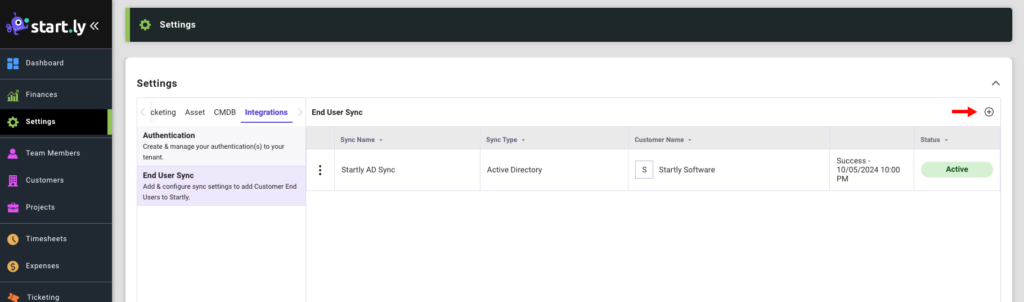
- Click on the Settings menu from the left nav.
- Select the Integrations category.
- Select the End User Sync setting.
- Click the + Icon to add a new sync configuration
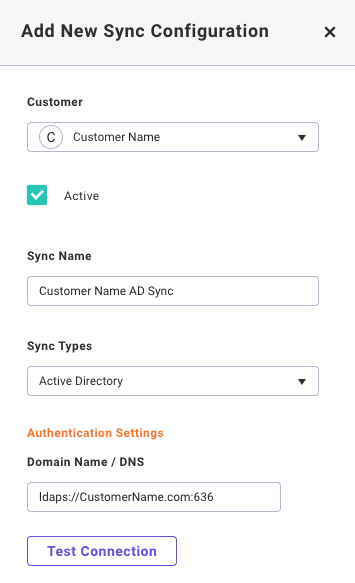
- Select a Customer
- Enter a Sync Name (e.g. Customer Name AD Sync)
- Select the Sync Type, either Active Directory or Okta
- Enter your Domain Name/DNS in LDAP URL for (e.g. ladps://CustomerName.com:636)
- Select Test Connection
Domain Name / DNS
URI (Uniform Resource Identifier) of the LDAP server. Server must have valid TLS certificate. URI must be specified in the following format:
• ldap://myldapserver.com:389
• ldaps://mysecureldapserver.com:636
If port is not specified explicitly, application will use default port
• LDAP – 389
• LDAPS – 636
If LDAPS is used, sever must be configured with a trusted TLS certificate which matches domain name and AD domain. Note: LDAP protocol without encryption and is not recommended to use outside of protected and trusted networks.
Test Authentication
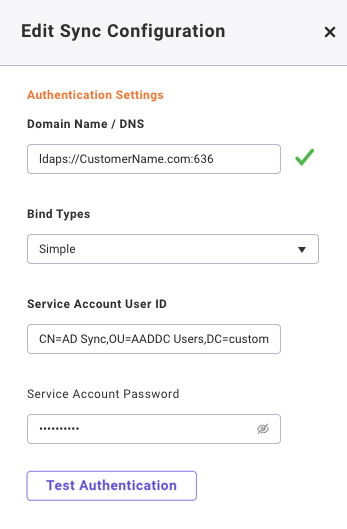
- Select a Bind Type to authenticate a client to a directory server
- Enter your Service Account User ID. See below for formatting.
- Enter your Service Account Password
- Select Test Authentication button
Bind Type
Simple – the login/password authentication. When this bind type is selected. Login and password is required
Anonymous – (Not Recommended) no authentication. Anonymous authentication is not supported by most providers and not secure.
Service Account User Id / Bind DN
Distinguished Name of the user (LDAP Admin) that have access to the directory. This field should be specified in format according to RFC 2253 https://datatracker.ietf.org/doc/html/rfc2253.
For Azure Active Directory Domain Services (AAD DS) it should be a member of AAD DC Administrators group. Example: CN=AD Sync,OU=AADDC Users,DC=CustomerName,DC=com
- CN – common name, the name of the user, usually looks like fname and lname combined but it might depend on specific AD configuration.
- OU – Organizational Unit. For ADD DS it will be AADDC Users
- DC – Domain Component – a sequence of domain name parts
Service Account Password / Bind Credential
Password string for the user
Finish Authentication Settings
- Enter your Users DN to search for users and groups
- By default the Username LDAP attribute, RDN LDAP attribute, UUID LDAP attribute, User object classes fields will be filled with default values
- Select Next to move on to Data Mappings
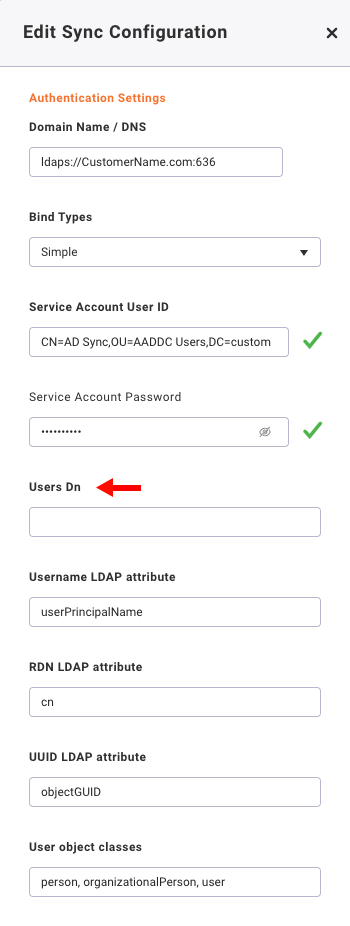
Users DN
Distinguished name of the object which contains all users to be synchronized. For AAD DS it will be:
OU=AADDC Users,DC=CustomerName,DC=com
Note: Startly’s current implementation performs only one level search so nested objects won’t be synchronized. But it Is possible to change to tree search.
Username LDAP attribute
The name of the LDAP attribute to be used as username. Must be unique. For AAD DS it will be userPrincipalName – contains username in email format. For Okta it will be uid. Usually, this parameter is automatically selected and don’t need to be changed by administrator in case of typical setup.
RDN LDAP Attribute
Name of the LDAP attribute, which is used as RDN (top attribute) of typical user DN. Usually it’s the same as the Username LDAP attribute, however it is not required. For example for Active directory, it is common to use ‘cn’ as RDN attribute when username attribute might be ‘sAMAccountName’. Usually, this parameter is automatically selected and don’t need to be changed by administrator in case of typical setup.
UUID LDAP Attribute
Name of the LDAP attribute, which is used as a unique object identifier (UUID) for objects in LDAP. For many LDAP server vendors, it is ‘entryUUID’; however, some are different. For example, for Active directory it should be ‘objectGUID’. If your LDAP server does not support the notion of UUID, you can use any other attribute that is supposed to be unique among LDAP users in tree. For example, ‘uid’ or ‘entryDN’. Usually, this parameter is automatically selected and don’t need to be changed by administrator in case of typical setup.
User object classes
All values of LDAP objectClass attribute for users in LDAP, divided by commas. For example: ‘inetOrgPerson, organizationalPerson’. Existing LDAP user records are found just if they contain all those object classes. It works as a filter by object class attribute.
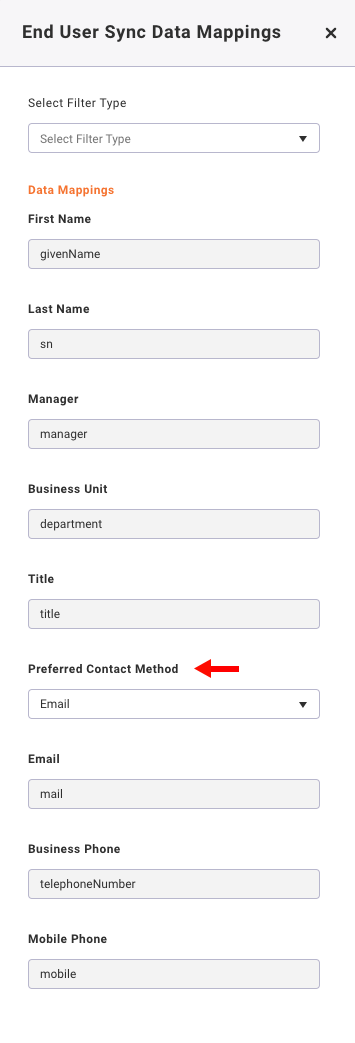
End User Sync Data Mappings (default)
- If your sync requires filtering skip to the next step
- The Preferred Contact Method mapping can be selected, by default email is selected
- All other Data Mappings for your sync are mapped by default
- Select Save
- A sync will be run automatically overnight (1AM EST)
- See Manual Sync to run a sync after setup
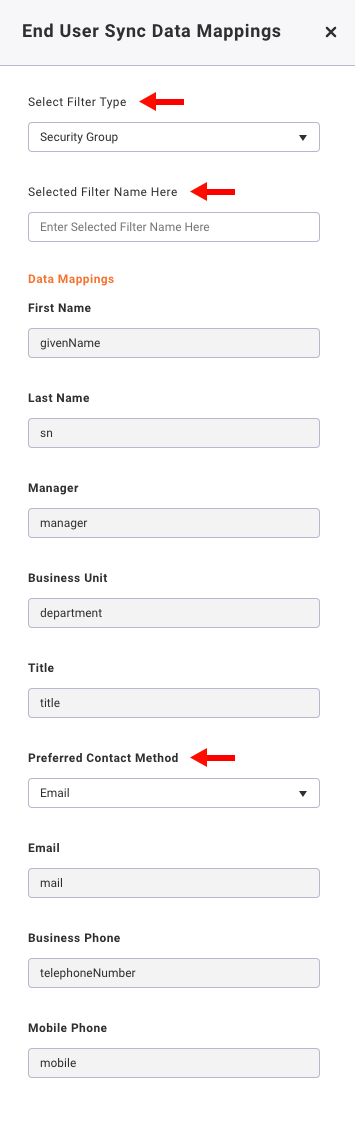
End User Sync Data Mappings (Filtered)
- If it is required to filter users by Group or OU, Select Filter Type (Security Group or OU)
- Enter the name of the Selected Filter Name from your Group or OU
- The Preferred Contact Method mapping can be selected, by default email is selected
- All other Data Mappings for your sync are mapped by default
- Select Save
- A sync will be run automatically overnight (1AM EST)
- See Manual Sync to run a sync after setup
Security group filter
Security group filter can be specified as semicolon separated list of groups the users must be members of. LDAP uses memberOf attribute of the user to search the users. Group can be specified by name or by DN. When group is specified by name, the group should be located in Users DN folder. If group is specified as DN it can be any valid group DN.
For example:
Security group: Administrators; Users
Users DN: OU=AADDC Users,DC=startly,DC=com
Resulting filter: (|(CN=Administrators,OU=AADDC Users,DC=startly,DC=com)(CN=Users,OU=AADDC Users,DC=startly,DC=com))
When group is specified as DN:
Security group: CN=Administrators,OU=IT,DC=startly,DC=com; Users
Users DN: OU=AADDC Users,DC=startly,DC=com
Resulting filter: (CN=Administrators,OU=IT,DC=startly,DC=com)(CN=Users,OU=AADDC Users,DC=startly,DC=com))
Note that in the second example Administrators group belongs to IT organizational unit.
It is allowed to use special characters and they will be escaped automatically. It is also possible to provide string with escape expressions.
Organizational Unit filter
OUs are specified as semicolon separated list of the organizational units to use for synchronization. The user will be synchronized in case when its DN contains at least one of the OUs specified in the list.
For example, if filter will be AADDS Users; IT
CN=John Snow, OU=AADDC Users,DC=CustmerName,DC=com – will be synchronized
CN=Thomas Anderson,OU=IT,DC=CustmerName,DC=com – will be synchronized
CN=Peter Parker,OU=Support,OU=IT, DC=CustmerName,DC=com – will be synchronized
CN=Harold McMillan,OU=Board,DC=CustmerName,DC=com = will NOT be synchronized
Example synchronization parameters
AAD DS
Connection URL: ldaps://ldaps.customername.com:636
Bind DN: CN=AD Sync,OU=AADDC Users,DC=startly,DC=com
Users DN: OU=AADDC Users,DC=startly,DC=com
Username LDAP attribute: userPrincipalName
RDN LDAP attribute: cn
UUID LDAP attribute: objectGUID
User object classes: person, organizationalPerson, user
Okta
LDAP Interface connection settings https://help.okta.com/en-us/content/topics/directory/ldap-interface-connection-settings.htm
Connection URL: ldaps://dev-12345678.ldap.okta.com
Bind DN: [email protected],dc=dev-12345678,dc=okta,dc=com
Users DN: ou=users, dc=dev-12345678, dc=okta, dc=com
Username LDAP attribute: uid
RDN LDAP attribute: cn
UUID LDAP attribute: uniqueIdentifier
User object classes: inetOrgPerson
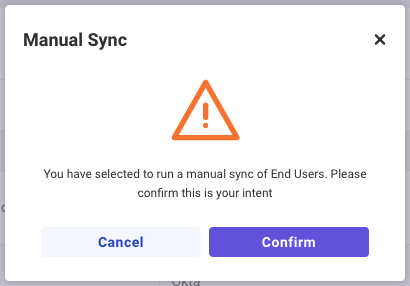
Manual Sync
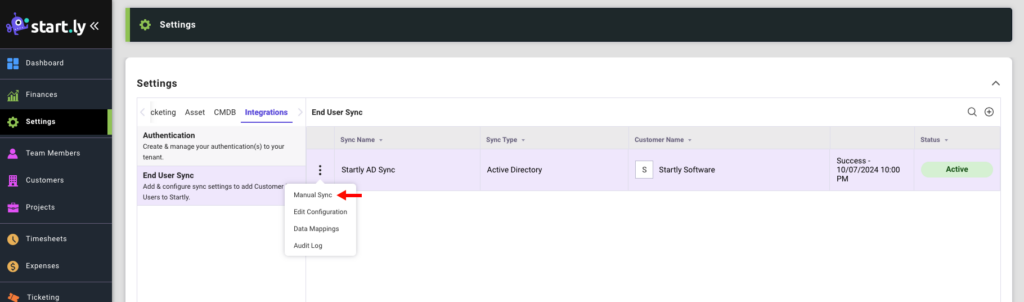
- To sync End Users outside of the scheduled overnight sync (1AM EST), select the Manual Sync option from the action menu of the End User Sync you wish to run in the list
- A confirmation modal appears, select Confirm to begin a manual sync